PHI is any sensitive patient information. This includes everything from name and address to a patients past current or even future health conditions.
 What Is Hipaa Privacy Rule Hippa Security Requirments Imperva
What Is Hipaa Privacy Rule Hippa Security Requirments Imperva
Transactions and Code Sets Standards Implementation Strategy.

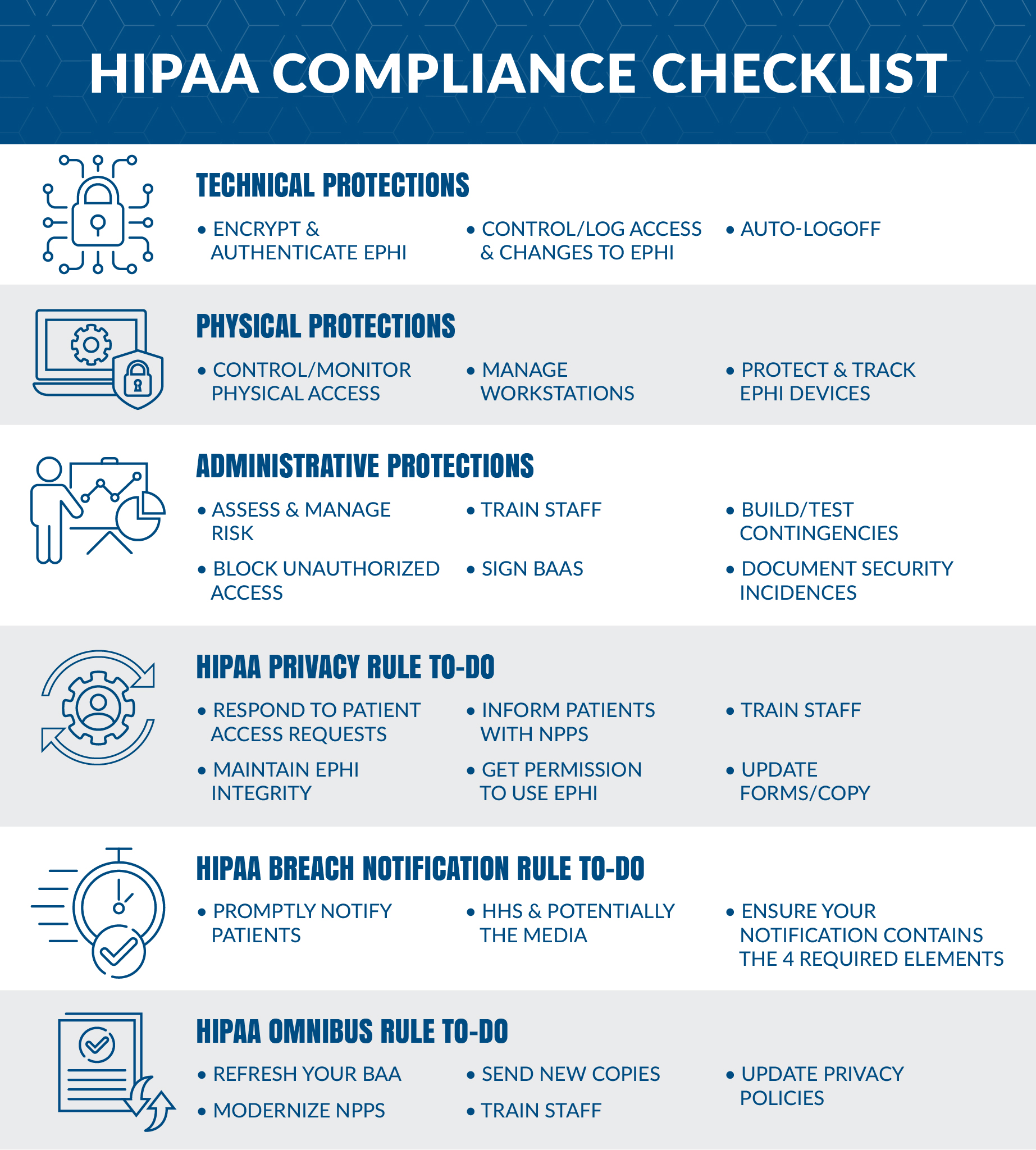
Hipaa security standards. The HIPAA Security Rule is a set of standards devised by the Department of Health Human Services HHS to improve the security of electronic protected health information ePHI and to ensure the confidentiality integrity and availability of ePHI at rest and in transit. The Act consists of rules governing protected health information PHI including Security Privacy. Security 101 for Covered Entities - PDF Administrative Safeguards - PDF Physical Safeguards - PDF.
This compliance is necessary for compliance with the HIPAA Security Rule. Ensure the confidentiality integrity and availability of all electronic protected health information the Covered Entity creates receives maintains or transmits Protect against any reasonably anticipated threats or hazards to the. The HIPAA Security Standards must be applied by health plans health care clearinghouses and health care providers to all health information that is maintained or transmitted electronically.
In the preamble to the Security Rule several NIST publications were cited as potentially valuable resources for readers with specific questions and concerns about IT security. Physical Safeguards The purpose of this implementation specification is to specifically align a persons access to information with his or her role or function in the organization. The HIPAA Security Rule requires these entities to implement appropriate safeguards to maintain the confidentiality integrity and availability of.
The HIPAA Security Standards must be applied by health plans health care clearinghouses and health care providers to all health information that is maintained or transmitted electronically. The HIPAA Security Information Series is a group of educational papers which are designed to give HIPAA covered entities insight into the Security Rule and assistance with implementation of the security standards. HIPAA Security Standards HIPAA established its security rule to keep PHI protected health information private and safe.
The full title of the HIPAA Security Rule decree is Security Standards for the Protection of Electronic Protected Health Information and as the official title suggests the ruling was created to define the exact stipulations required to safeguard electronic Protected Health Information ePHI specifically relating to how the information is stored and transmitted between digital devices. HIPAA security standards sometimes referred to as HIPAA security procedures are a series of requirements covered entities and business associates must comply with. The Security Rule requires appropriate administrative physical and technical safeguards to ensure the confidentiality integrity and security of electronic protected health information.
HIPAA compliance data storage rules are meant to. The HIPAA Security Rule establishes national standards to protect individuals electronic personal health information that is created received used or maintained by a covered entity. Go to the Security Standards page.
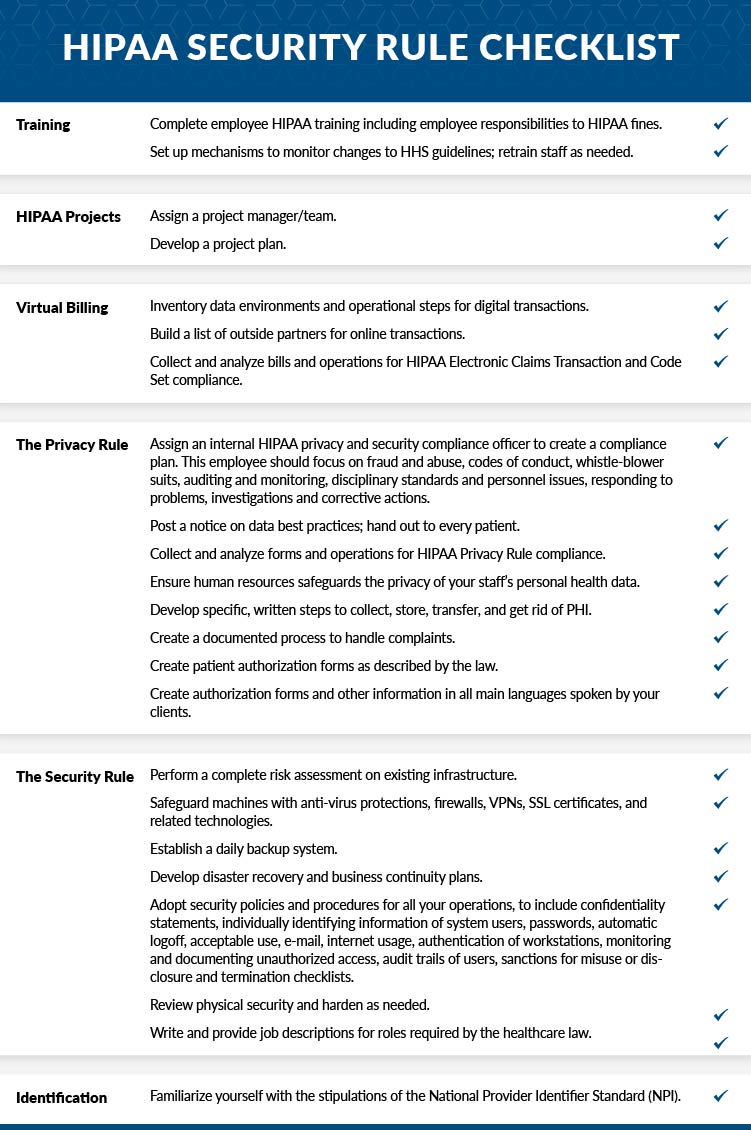
These standards known as the HIPAA Security Rule were published on February 20 2003. HIPAA is a set of standards introduced by the US. HIPAA Survival Guide Note This standard contains one required specification regarding identifying and responding to suspected or known security incidents.
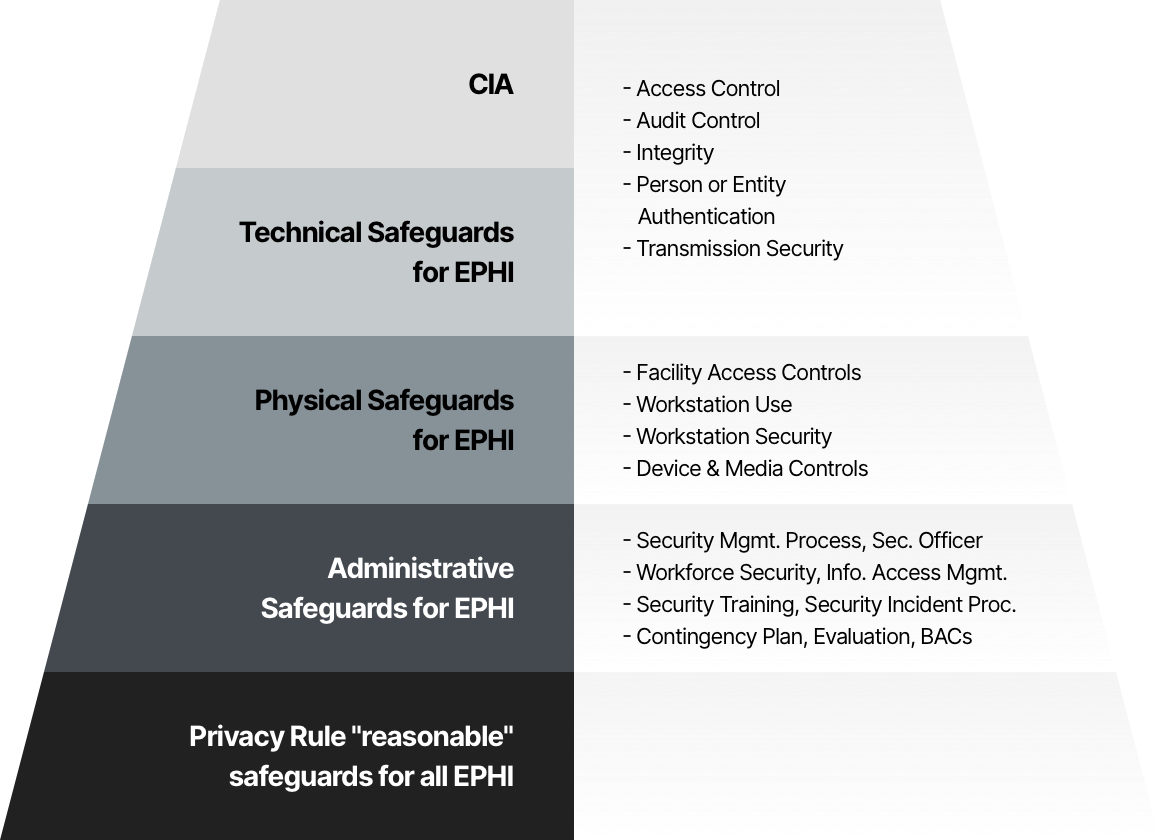
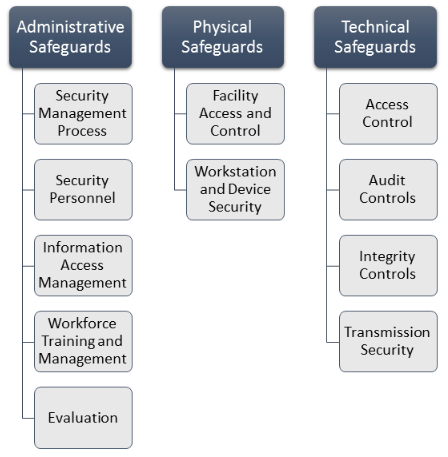
HIPAA SECURITY STANDARDS PHYSICAL SAFEGUARDS -Facility Access Controls -Workstation Use -Workstation Security -Device and Media Controls TECHNICAL SAFEGUARDS - Access Control - Audit Controls - protected health information and control access to itIntegrity - Person or Entity Authentication - Transmission Security ORGANIZATIONAL. The standards are intended to protect both the system and the information it contains from unauthorized access and misuse. The Security Standards for the Protection of Electronic Protected Health Information the Security Rule establish a national set of security standards for protecting certain health information that is held or transferred in electronic form.
The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards.
 Hipaa Compliance Checklist What Is Hipaa Compliance
Hipaa Compliance Checklist What Is Hipaa Compliance
 What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
 Breaking Down The Hipaa Security Rule Accountable Accountable
Breaking Down The Hipaa Security Rule Accountable Accountable
 What Is Hipaa Legend Networking
What Is Hipaa Legend Networking
 Hipaa Security Rule Checklist What Is The Hipaa Security Rule
Hipaa Security Rule Checklist What Is The Hipaa Security Rule
 What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
 Understanding The Hipaa Security Rule Skoda Minotti Risk Advisory Services
Understanding The Hipaa Security Rule Skoda Minotti Risk Advisory Services
 Handling Sensitive Patient Data In The Us Guide To Hipaa Compliance Pharma It
Handling Sensitive Patient Data In The Us Guide To Hipaa Compliance Pharma It
 What Is The Hipaa Security Rule Quora
What Is The Hipaa Security Rule Quora
 Hipaa Security Rule Simplified Breachlock
Hipaa Security Rule Simplified Breachlock
 What Healthcare Providers Must Know About The Hipaa Security Rule
What Healthcare Providers Must Know About The Hipaa Security Rule
 What Is Hipaa Compliance Your 2021 Guide Checklist Varonis
What Is Hipaa Compliance Your 2021 Guide Checklist Varonis
 Lions Tigers And Bears Navigating Hipaa Compliant File Sharing Smartfile
Lions Tigers And Bears Navigating Hipaa Compliant File Sharing Smartfile
Hipaa Security Rule Hipaa Academy Beyond Hipaa Hitech Mu Ehr Health It Health Insurance Portability And Accountability Act

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.